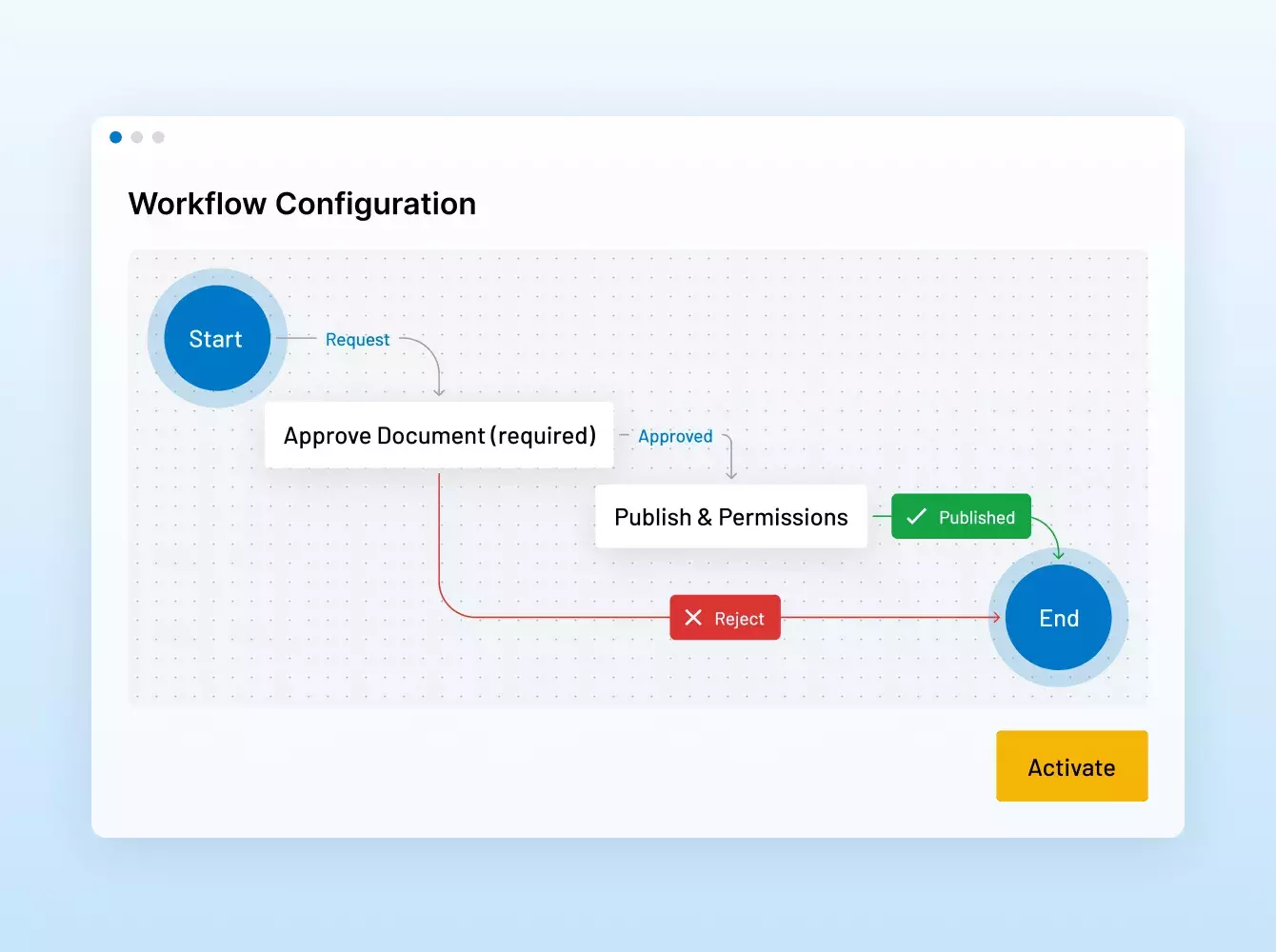
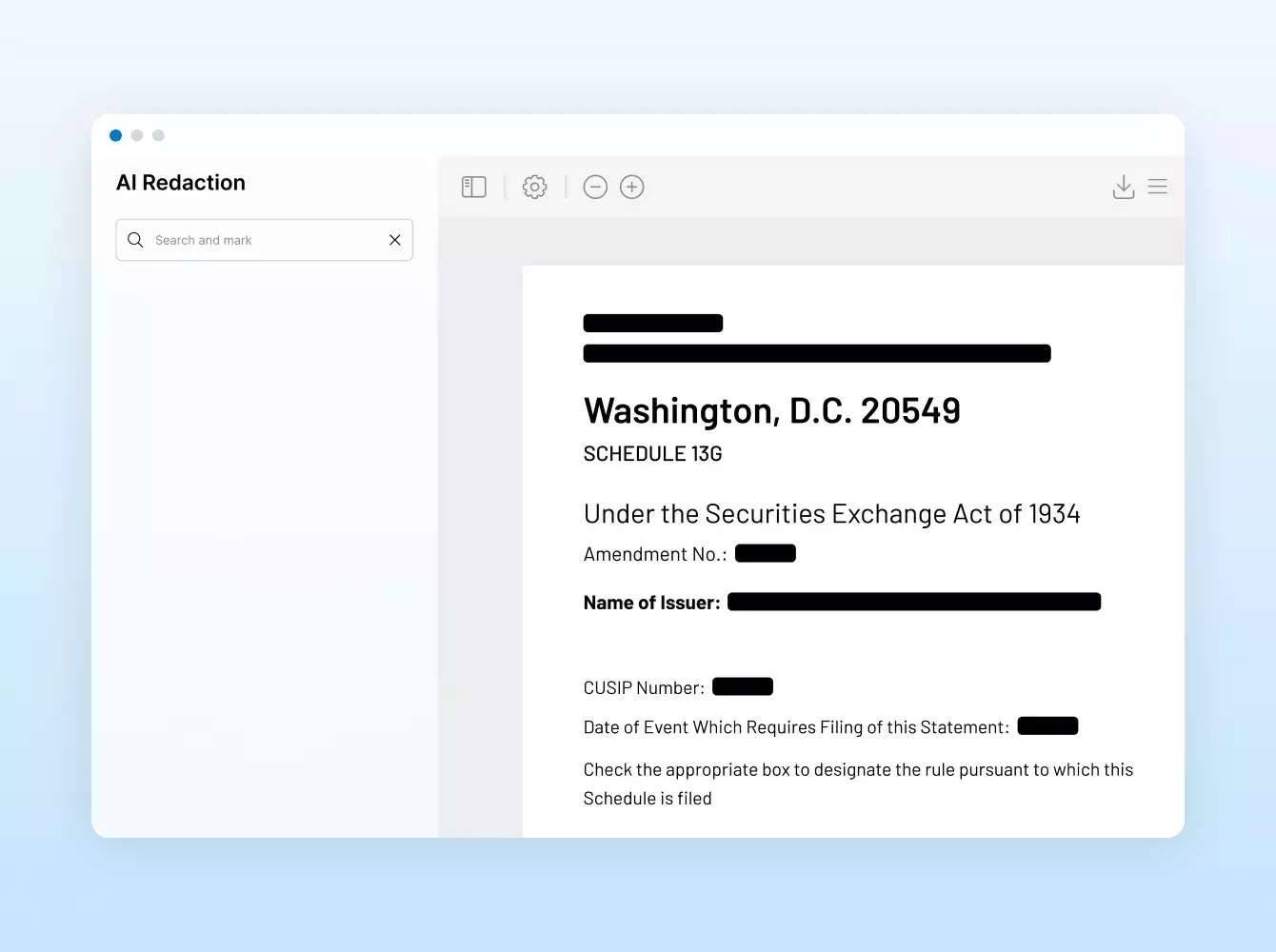
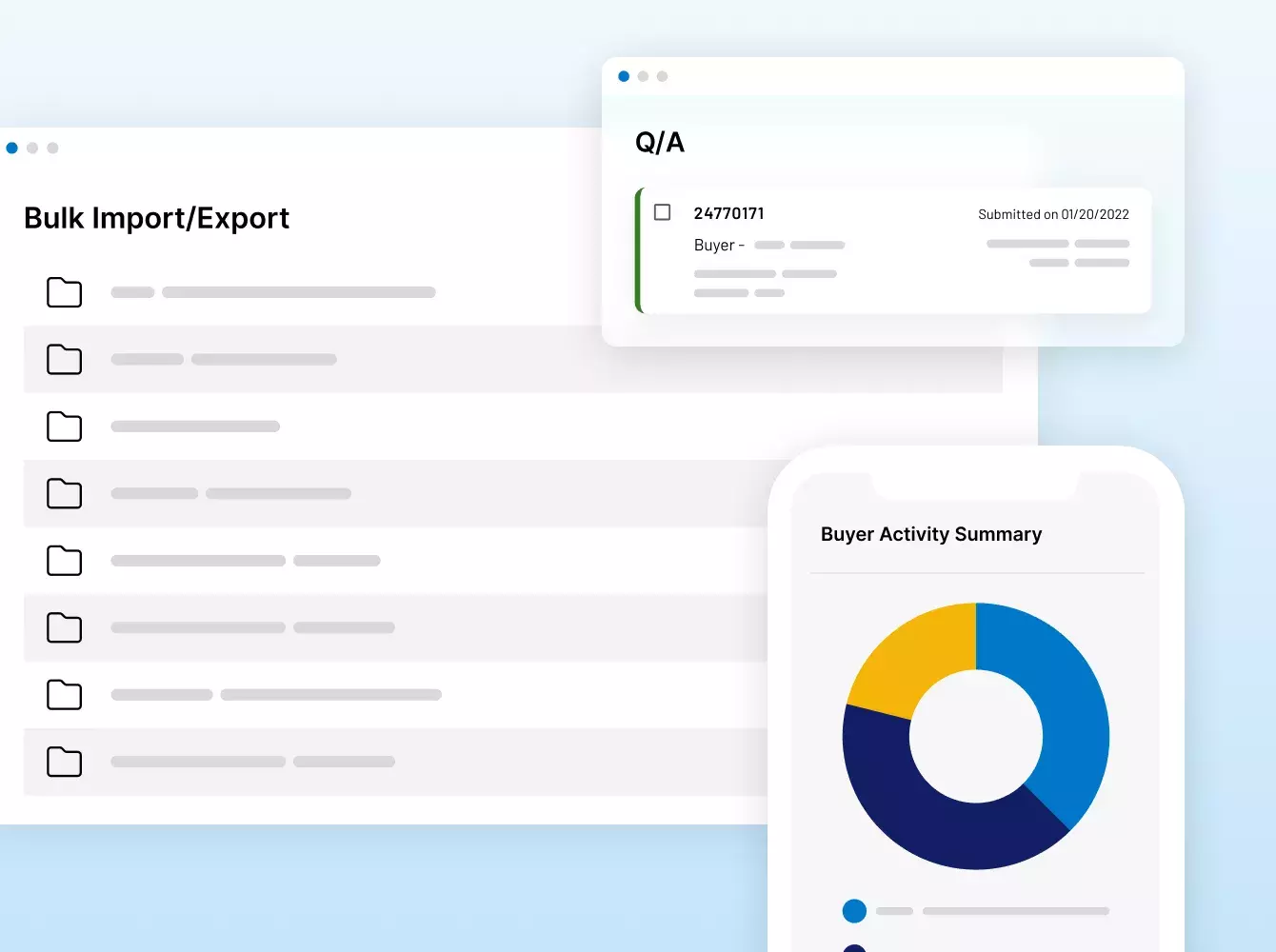
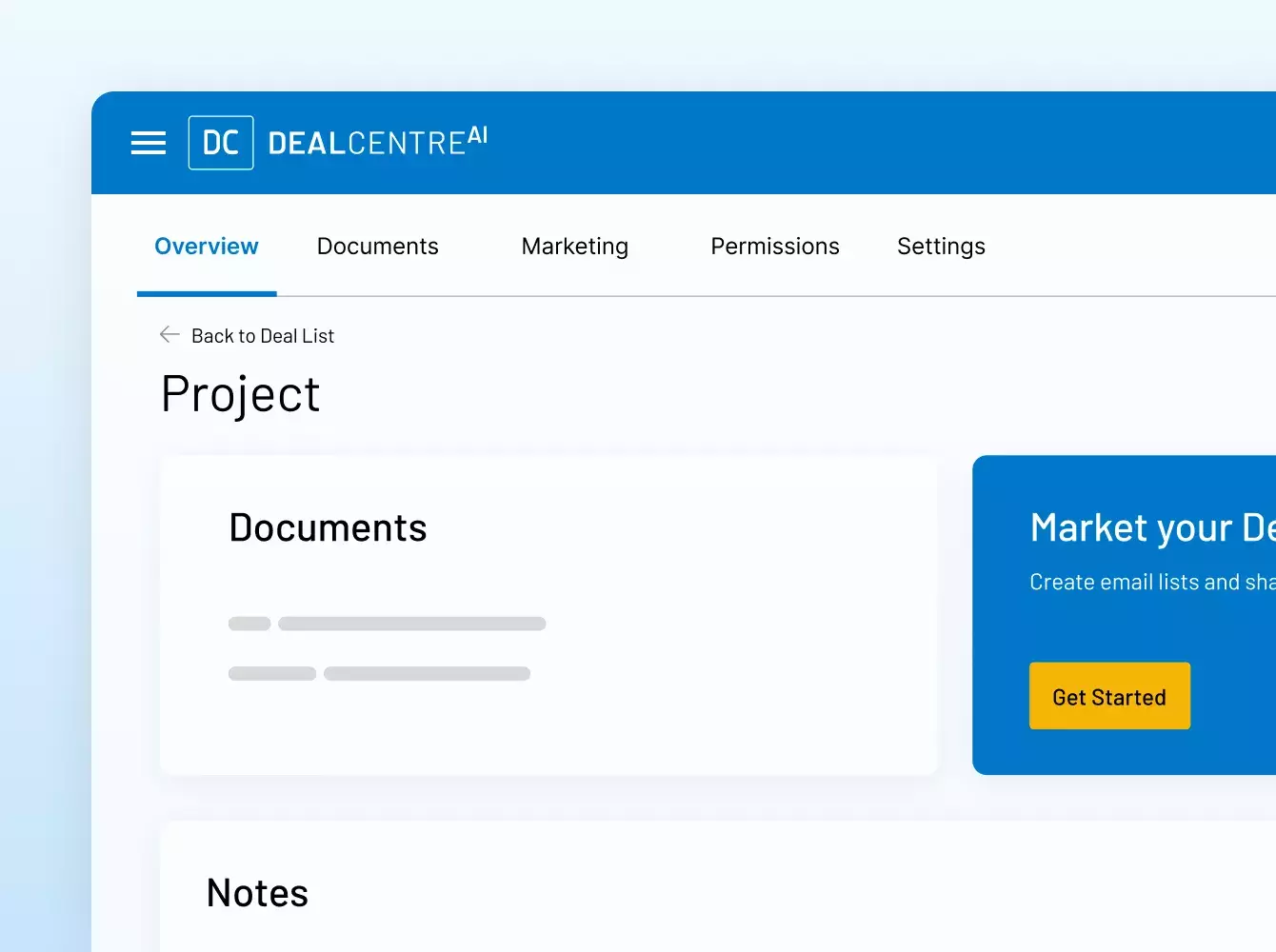
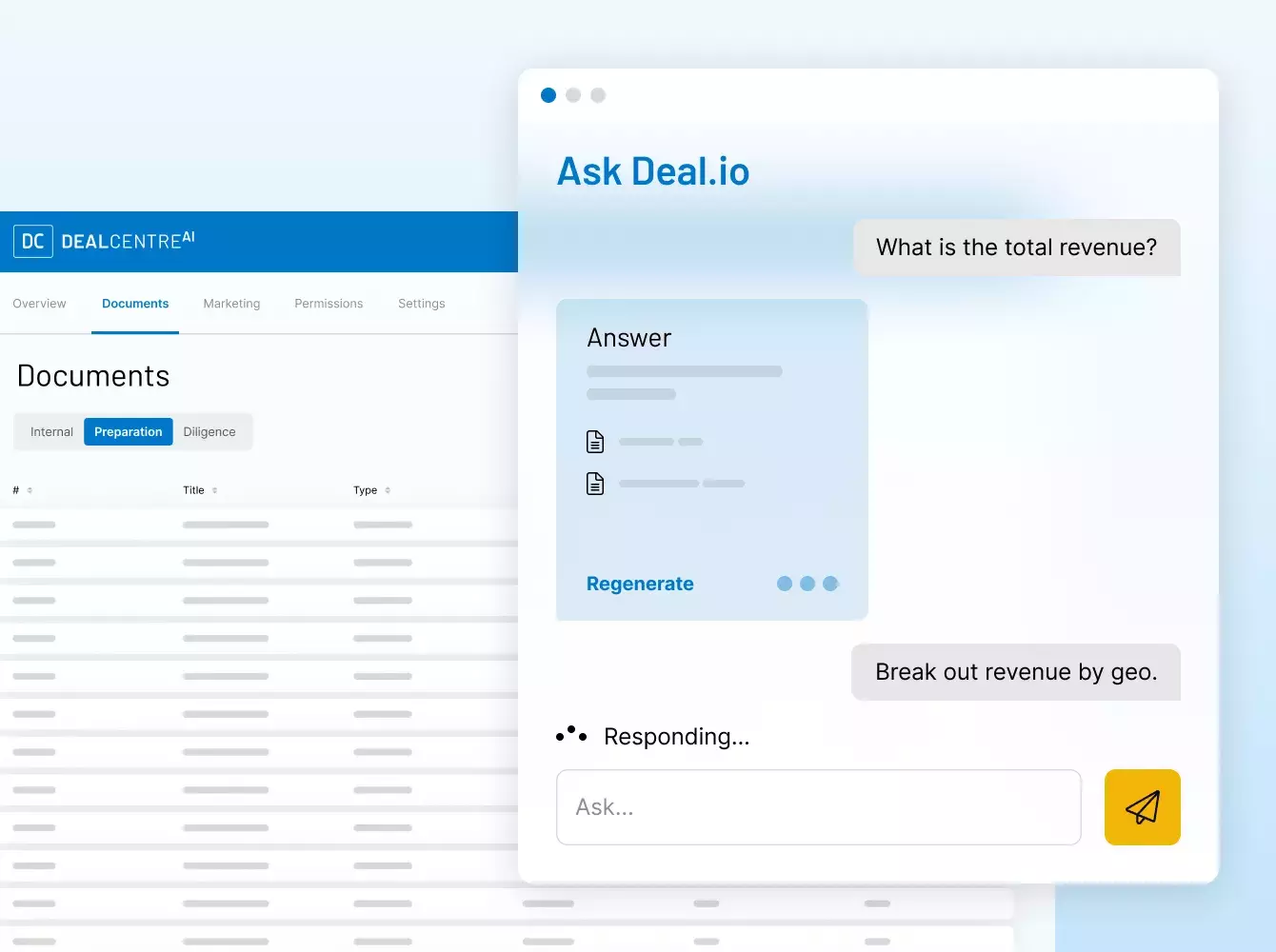
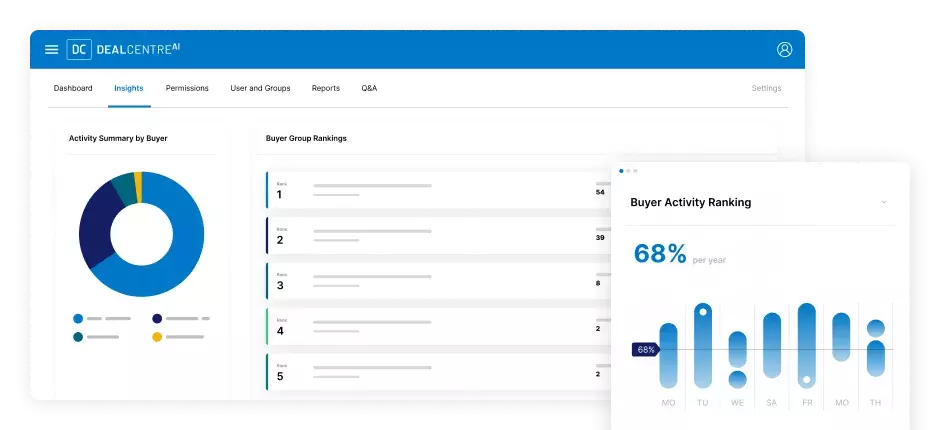
ディール 資金調達 IPO シンジケーション 融資
をインテリジェントに
こなす。
MAバーチャルデータルームやシンジケートローンから資金調達、投資家のオンボーディング、ファンドレポートなど、抜群のセキュリティと効率性で戦略的な金融ディールを強化。
Fortune 500および大手マーケットメーカーからの信頼

Raytheon
$ 89.8B
SS&C イントラリンクスは、United TechnologiesによるRaytheonの買収をサポートし、89.8Bを調達。

Dow
$ 57.3B
SS&C イントラリンクスは、Dow Holdings Inc.の57.3億ドルのスピンオフをサポート。

Anaplan
$ 10.3B
SS&C イントラリンクスは、Thoma BravoによるAnaplanの103億ドルの買収をサポート。

Whole Foods
$ 13.6B
SS&C イントラリンクスは、AmazonによるWhole Foodsの13.6億ドルの買収をサポート。

Fortress
$ 3.3B
SS&C イントラリンクスは、ソフトバンクによるFortress Investment Groupの33億ドルの買収をサポート。

TSG Consumer
$ 6B
SS&C イントラリンクスは、消費者向け製品セクターに焦点を当てたバイアウトファンドであるTSGのファンドTSG9の資金調達をサポート。
Neuberger Berman
$ 2.5B
SS&C イントラリンクスは、NeubergerのNB Credit Opportunities Fund IIの資金調達をサポート。

Riverside
$ 1.87B
SS&C イントラリンクスは、RiversideのMicro-Cap Fund VIの資金調達をサポート。

Hayfin
$ 6.61B
SS&C イントラリンクスは、HayfinのDirect Lending Fund IVの資金調達をサポート。

Summit Partners
$ 1.52B
SS&C イントラリンクスは、Summit PartnerのEurope Growth Equity Fund IVの資金調達をサポート。
世界で信頼されている
金融テクノロジー
プロバイダー
イントラリンクスは20年以上前にVDRを開拓し、以来革新を続けています。弊社のソリューションは、世界最大の資本市場の取引を強化し、GPに世界クラスのLP体験をお届けします。
お問い合わせ#1 M&A
35兆ドル以上の金融取引で ソリューションを提供
#1 GP-LP
10万以上の組織の515,000の個人とのコミュニティ
#1
資金調達プラットフォーム
世界的に調達した$2のうち$1以上
$200M+
過去5年間の研究開発投資額
ISO 27701
最高レベルのデータプライバシー認定を初めて取得したVDRプロバイダ
6
秒。受賞歴のあるサポートチームに平均6秒でおつなぎします。
Need to advise your client
on how to choose a VDR?
Advisors often need to present their clients with a comparison of VDR alternatives. To save you time, we built a template that includes a feature comparison between top VDR providers.

データを安全に保管する場所が必要なのはなぜですか?
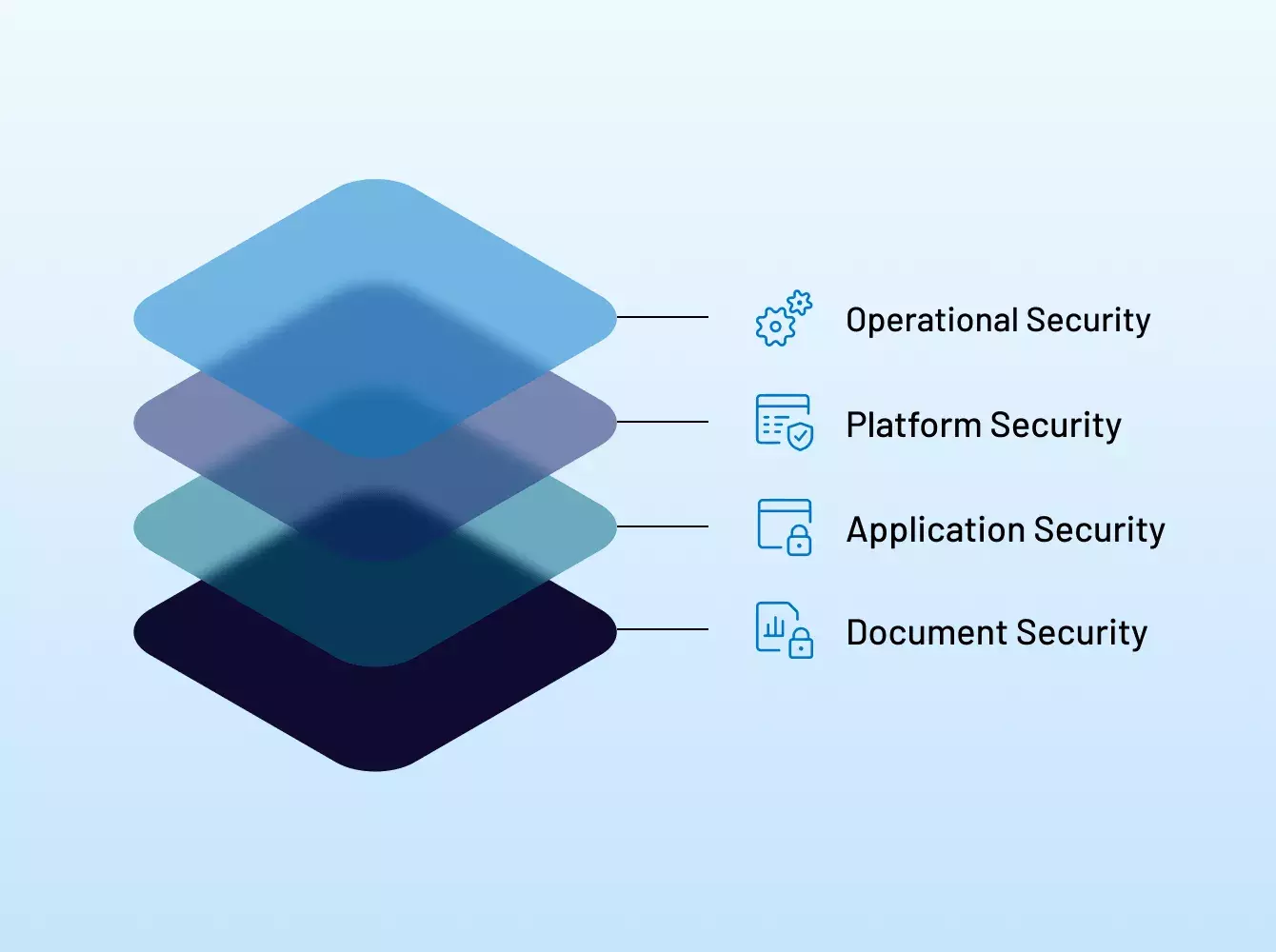
金融取引には多数のドキュメントのやり取りが発生し、その多くは機密情報を含む機密文書です。そのため、信頼できる実績のあるプロバイダーを選択することが重要です。イントラリンクスの使命は、お客様、顧客およびパートナーのセキュリティエコシステム内の取引とデータを保護することです。
どのようなサービスを提供していますか?
イントラリンクスのサービスチームは、VDR設定に特化した戦術的な支援、マスキング機能やNDAなどの面倒なタスクに特化したリソース、自動化と複雑な統合でも可能にする完全にカスタマイズされたソリューションなど、ニーズにいつでもお応えいたします。
先駆的な技術、業界の専門知識、および数十年にわたる経験を駆使して開発された弊社のサービスは、取引またはプロジェクトのあらゆる段階、要件に対応いたします。
他のプロバイダーよりも優れている点は何ですか?
バーチャルデータルーム(VDR)のパイオニアであるイントラリンクスは、データと評判を保護するために、専用ソリューションおよび強固なセキュリティを使用し、お客様の作業方法を継続的に革新しています。
弊社は、60億ドル以上の収益を上げているフィンテック企業であるSS&Cの支援を受けています。
競合他社は研究開発とサービスを縮小していますが、弊社は5年間で2億ドル以上の投資を行い、お客様にワールドクラスの体験を提供しております。
他のプロバイダーのファイル共有ソリューションも、同様に安全ではありませんか?
多くのプロバイダーは、安全なソリューションを提供していると主張しつつも、意図的にあいまいな表現を使用し、真のセキュリティ情報をマスキングしています。弊社の包括的なセキュリティアプローチには、イントラリンクスの人員、プロセスおよびサポートインフラストラクチャのあらゆる側面に及ぶ、業界をリードする認定とコンプライアンスのベストプラクティスが含まれています。
Latest INsights
Industry-leading thought leadership, insights, events and resources.