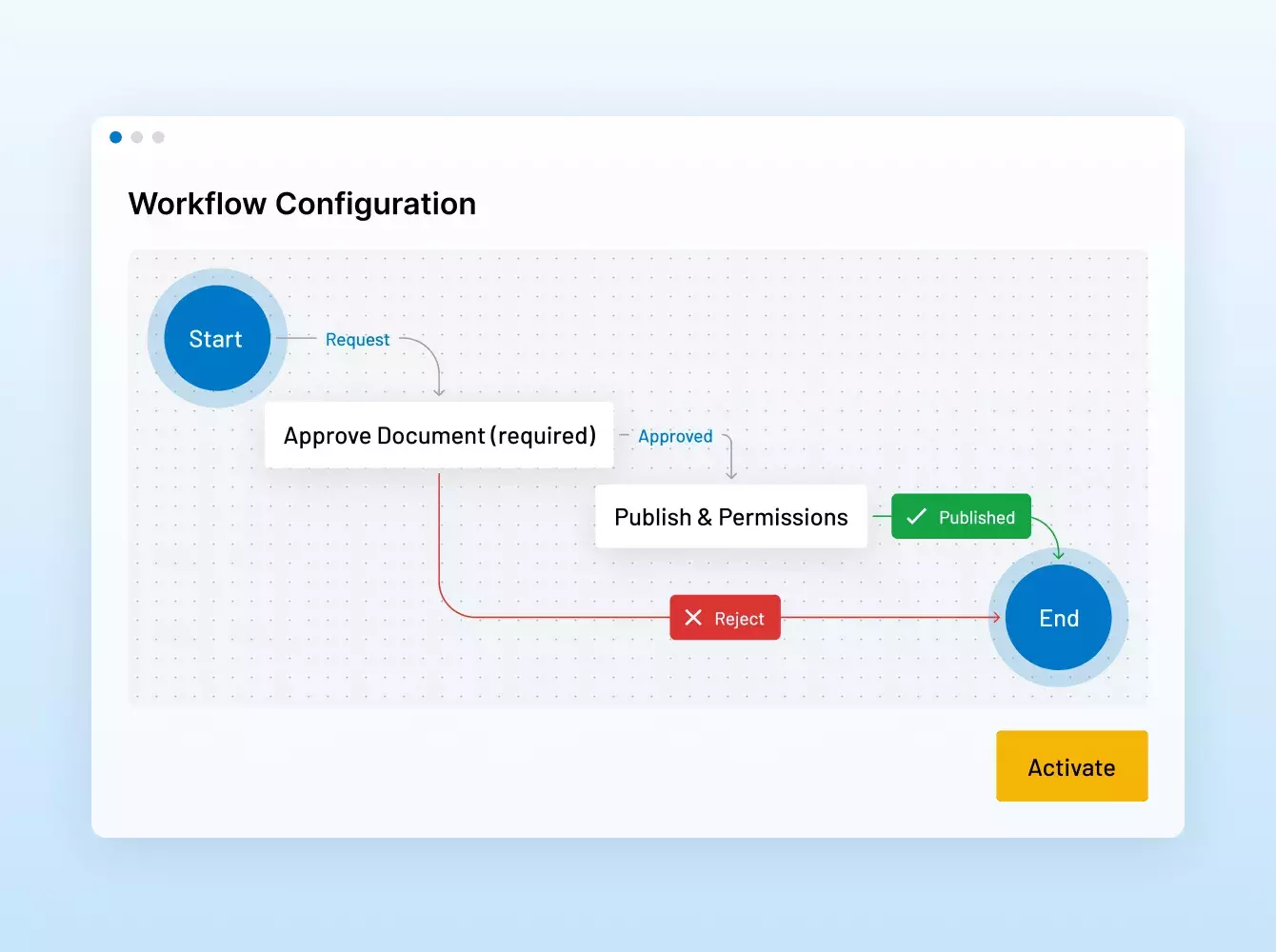
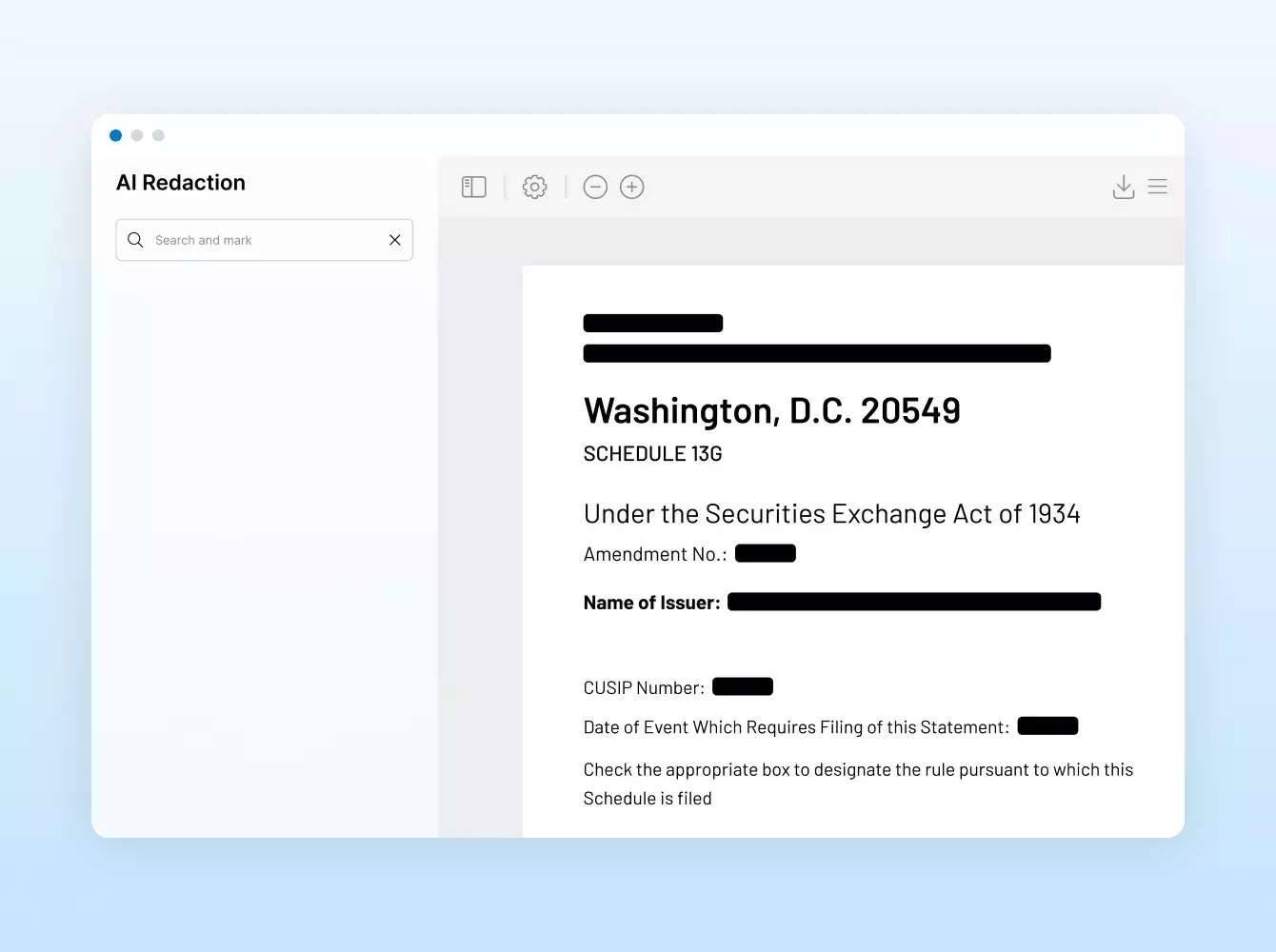
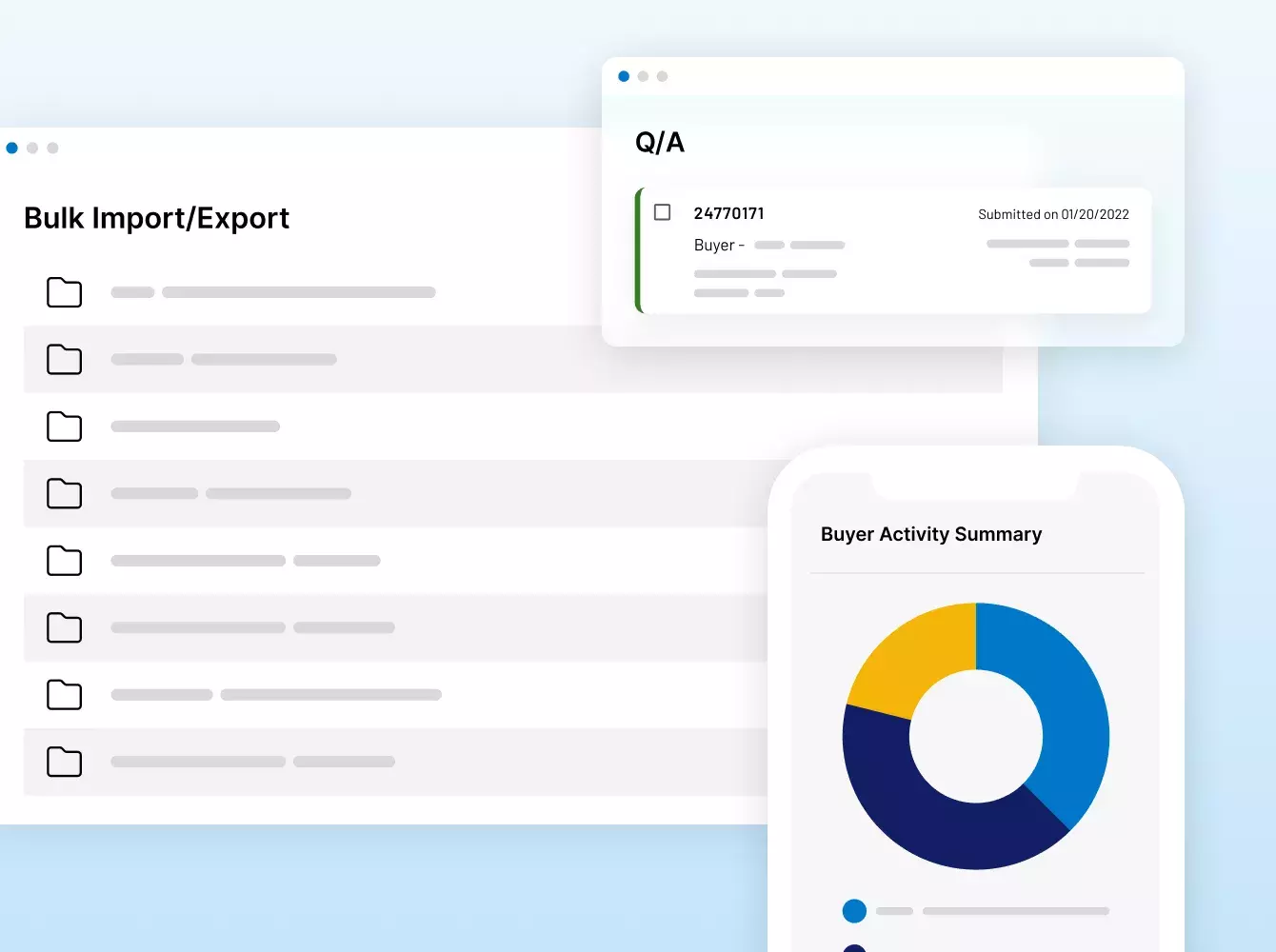
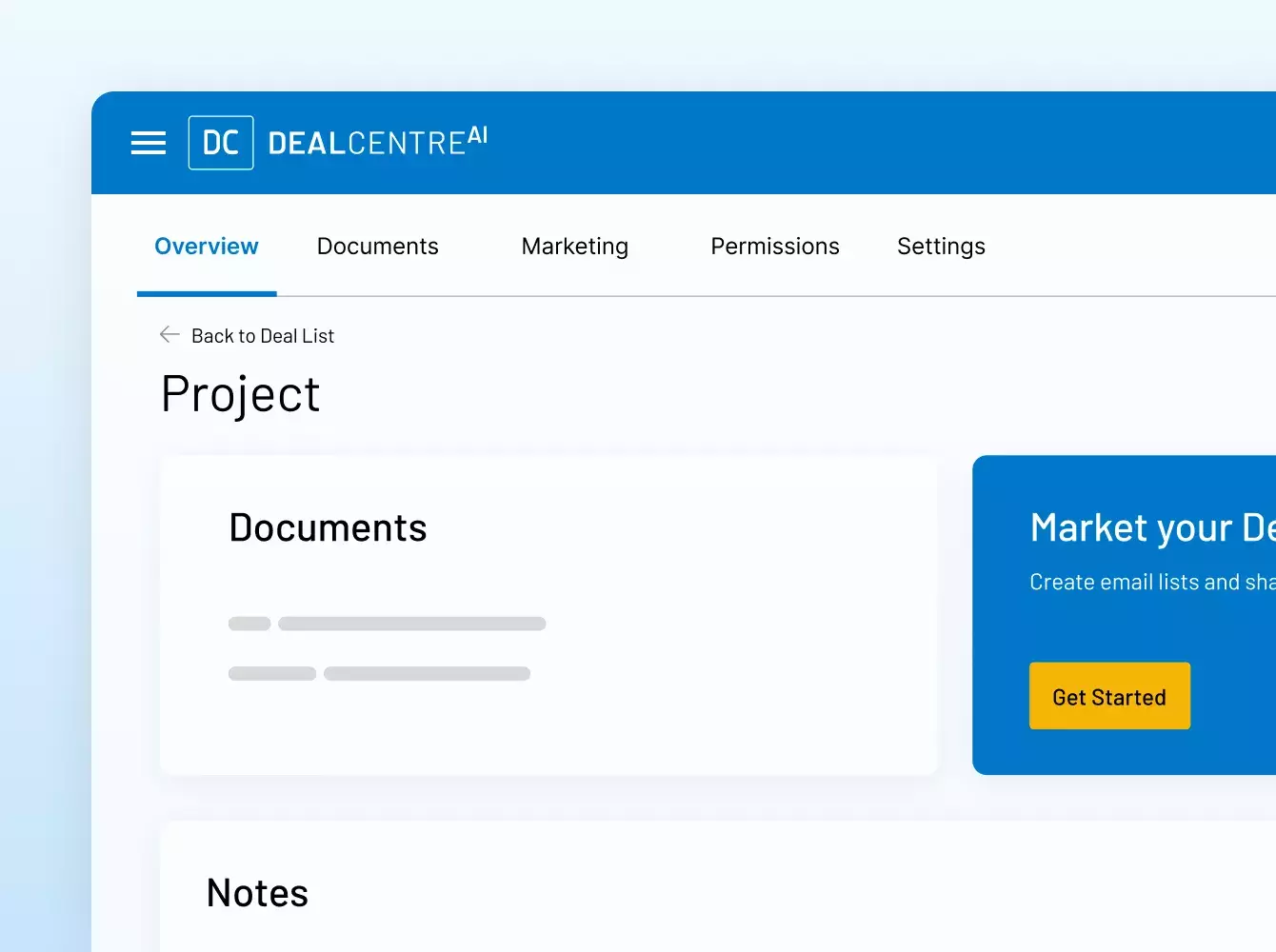
Donde sus sindicaciones se hacen realidad. Con inteligencia.
Potenciamos sus operaciones financieras estratégicas con una seguridad y una eficiencia inigualables, desde virtual data rooms de MA y préstamos sindicados hasta recaudación de fondos, incorporación de inversionistas, informes de fondos y mucho más.
Con la confianza de las empresas Fortune 500 y los mayores creadores de mercado

Raytheon
$ 89.8B
SS&C Intralinks facilitó la adquisición de Raytheon por parte de United Technologies por 89,800 millones.

Dow
$ 57.3B
SS&C Intralinks facilitó la separación subsidiaria por $57,300 millones de Dow Holdings Inc. a los accionistas.

Anaplan
$ 10.3B
SS&C Intralinks facilitó la adquisición por $10,300 millones de Anaplan por parte de Thoma Bravo.

Whole Foods
$ 13.6B
SS&C Intralinks facilitó la adquisición de Whole Foods por parte de Amazon por 13,600 millones.

Fortress
$ 3.3B
SS&C Intralinks facilitó la adquisición por 3,300 millones de Fortress Investment Group por parte de SoftBank.

TSG Consumer
$ 6B
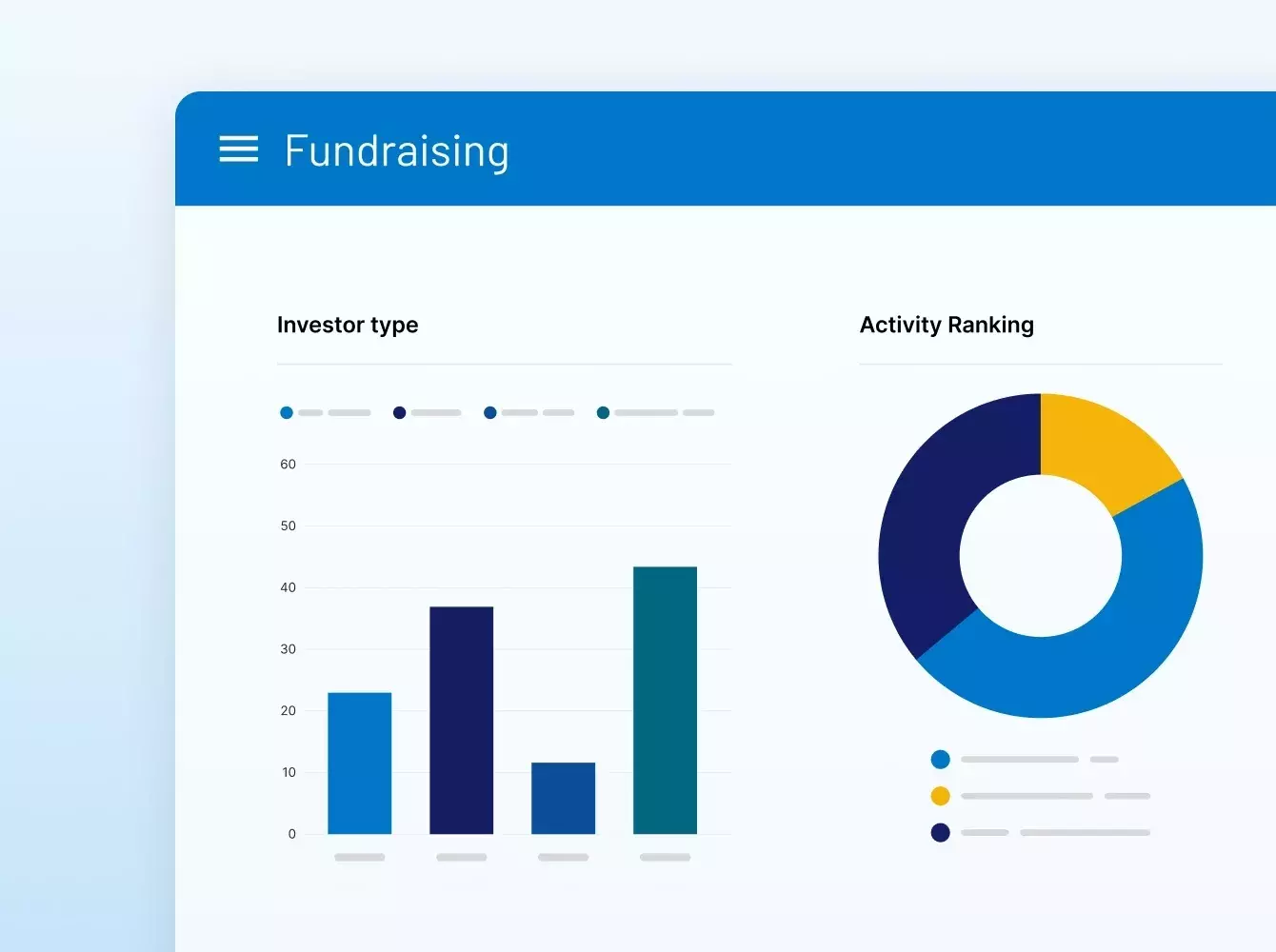
SS&C Intralinks facilitó la recaudación de fondos para el fondo TSG9 de TSG, un fondo de adquisición centrado en el sector de consumo.
Neuberger Berman
$ 2.5B
SS&C Intralinks facilitó la recaudación de fondos para el fondo NB Credit Opportunities Fund II de Neuberger.

Riverside
$ 1.87B
SS&C Intralinks facilitó la recaudación de fondos para el fondo Micro-Cap Fund VI de Riverside.

Hayfin
$ 6.61B
SS&C Intralinks facilitó la recaudación de fondos para el fondo Direct Lending Fund IV de Hayfin.

Summit Partners
$ 1.52B
SS&C Intralinks facilitó la recaudación de fondos para el fondo Europe Growth Equity Fund IV de Summit Partner.

Summit Partners
$ 1.52B
SS&C Intralinks facilitó la recaudación de fondos para el fondo Europe Growth Equity Fund IV de Summit Partner.
El proveedor de tecnología financiera de confianza
de todo el mundo.
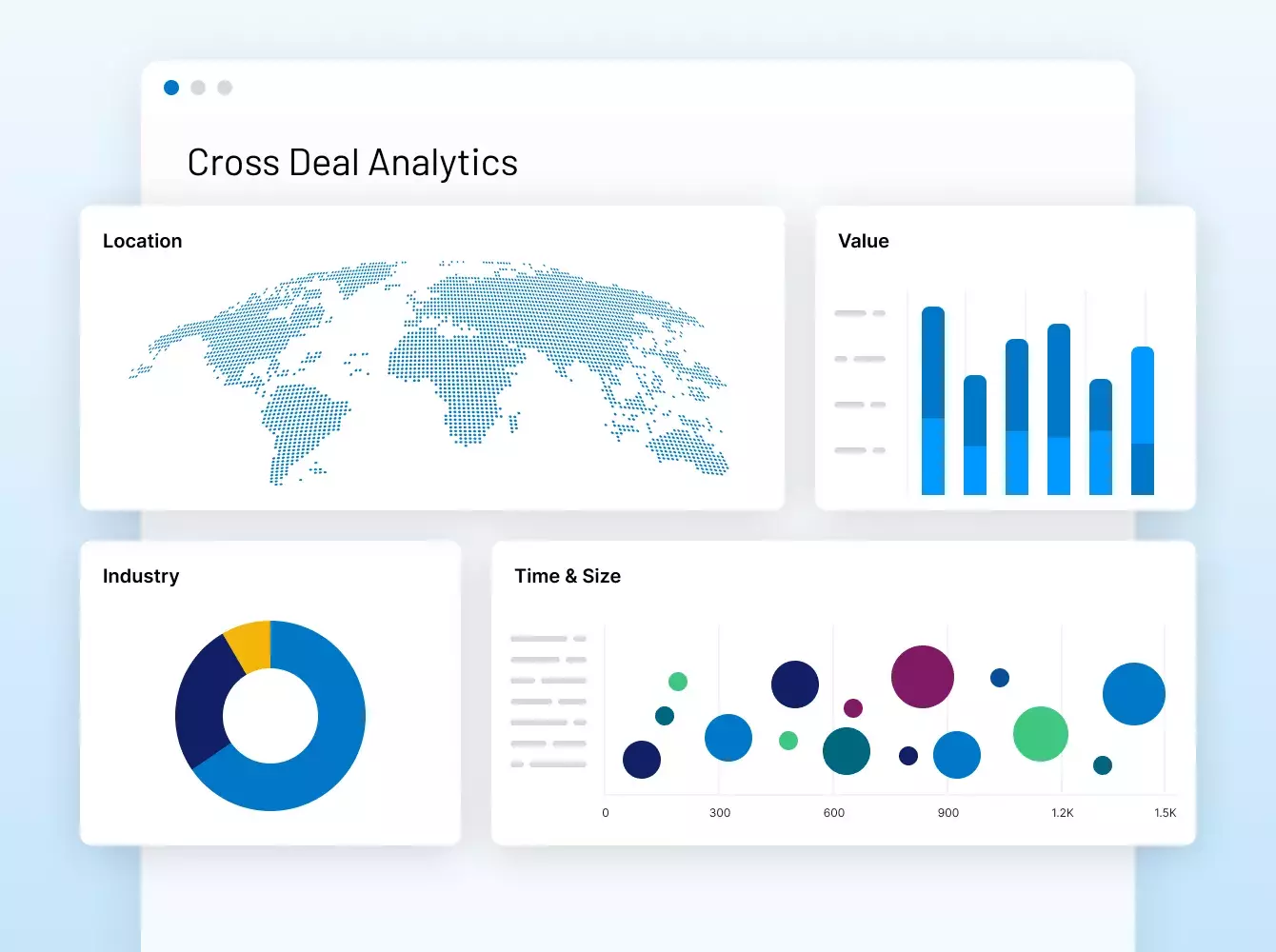
Intralinks fue pionera en el uso de VDR hace 20 años y sigue innovando desde Nuestras soluciones impulsan los deals de los mercados de capitales más grandes del mundo y permiten a los GP ofrecer experiencias de LP de gran nivel.
Contáctenos#1 M&A
soluciones para deals con más de $35 billones de transacciones financieras
#1 GP-LP
Comunidad con 515000 usuarios provenientes de más de 100,000 organizaciones
#1
Plataforma de recaudación de fondos
Más de $1 de cada $2 USD recaudados en todo el mundo
Más de $200 m
En inversion en R&D en los últimos 5 años
ISO 27701
Primer proveedor de VDR en obtener la certificación más alta en privacidad de datos
6
Segundos, el tiempo promedio que lleva comunicarse con nuestro galardonado equipo de soporte al cliente
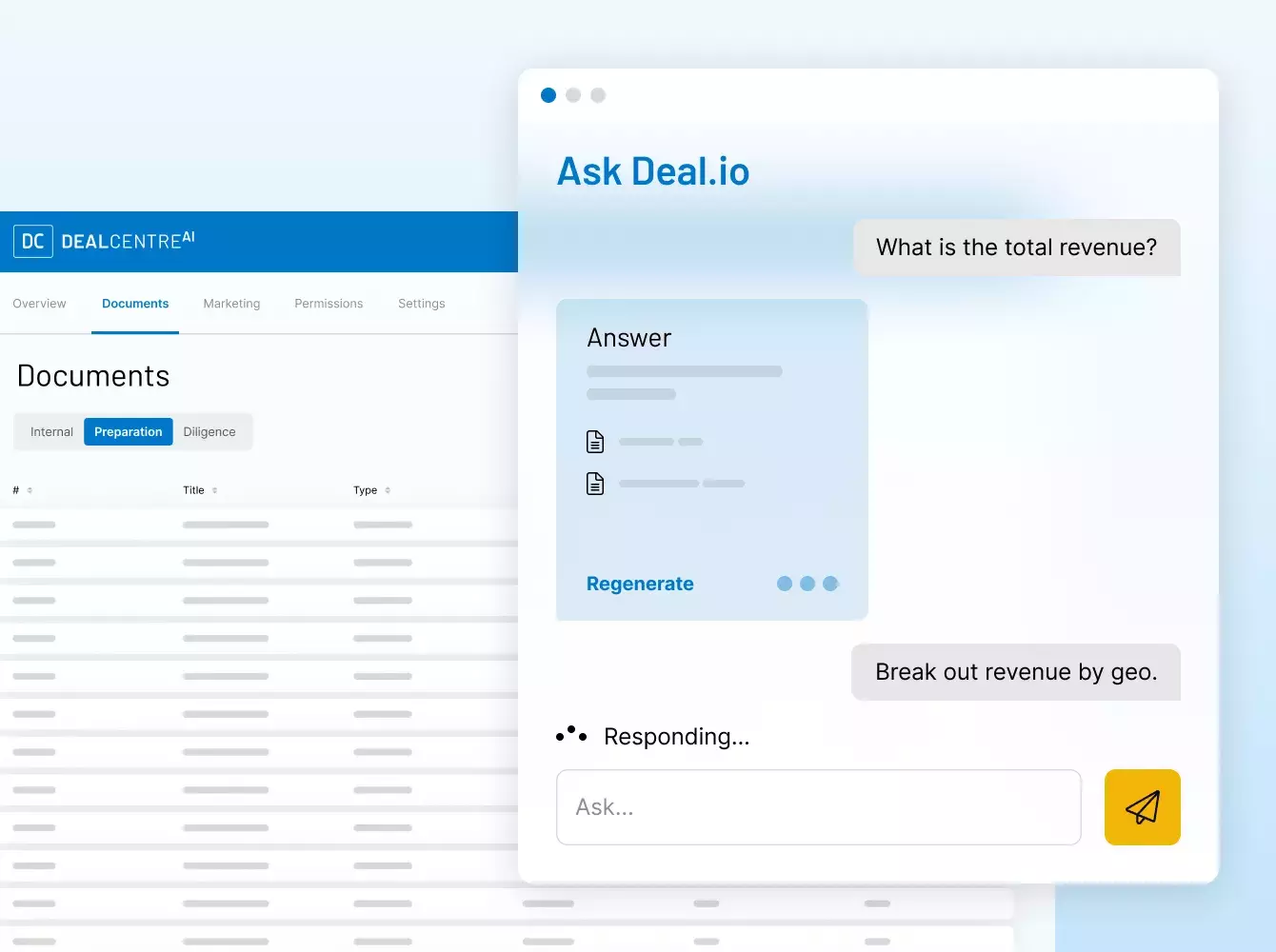
¿Por qué necesito un lugar seguro para mis datos?
Las transacciones financieras conllevan una gran cantidad de documentos, muchos de los cuales son confidenciales e incluyen información delicada.
Elegir a un proveedor de confianza y con experiencia es esencial. En Intralinks, nuestra misión es proteger su deal y sus datos mediante un ecosistema dedicado a la seguridad para usted, sus clientes y sus socios.
¿Qué servicios adicionales ofrecen?
Si nuestros clientes necesitan asistencia táctica para configurar un VDR, recursos extra para realizar tareas tediosas como la redacción de documentos o acuerdos de no divulgación, o una solución totalmente personalizada con automatización e integraciones complejas, los equipos de servicios de Intralinks están listos para ayudar.
Nuestra propuesta de servicios combina nuestra tecnología pionera, un conocimiento especializado en la industria y décadas de experiencia para cumplir con todos los requisitos en cada etapa de un deal o proyecto.
¿Por qué son una mejor opción frente a otros proveedores?
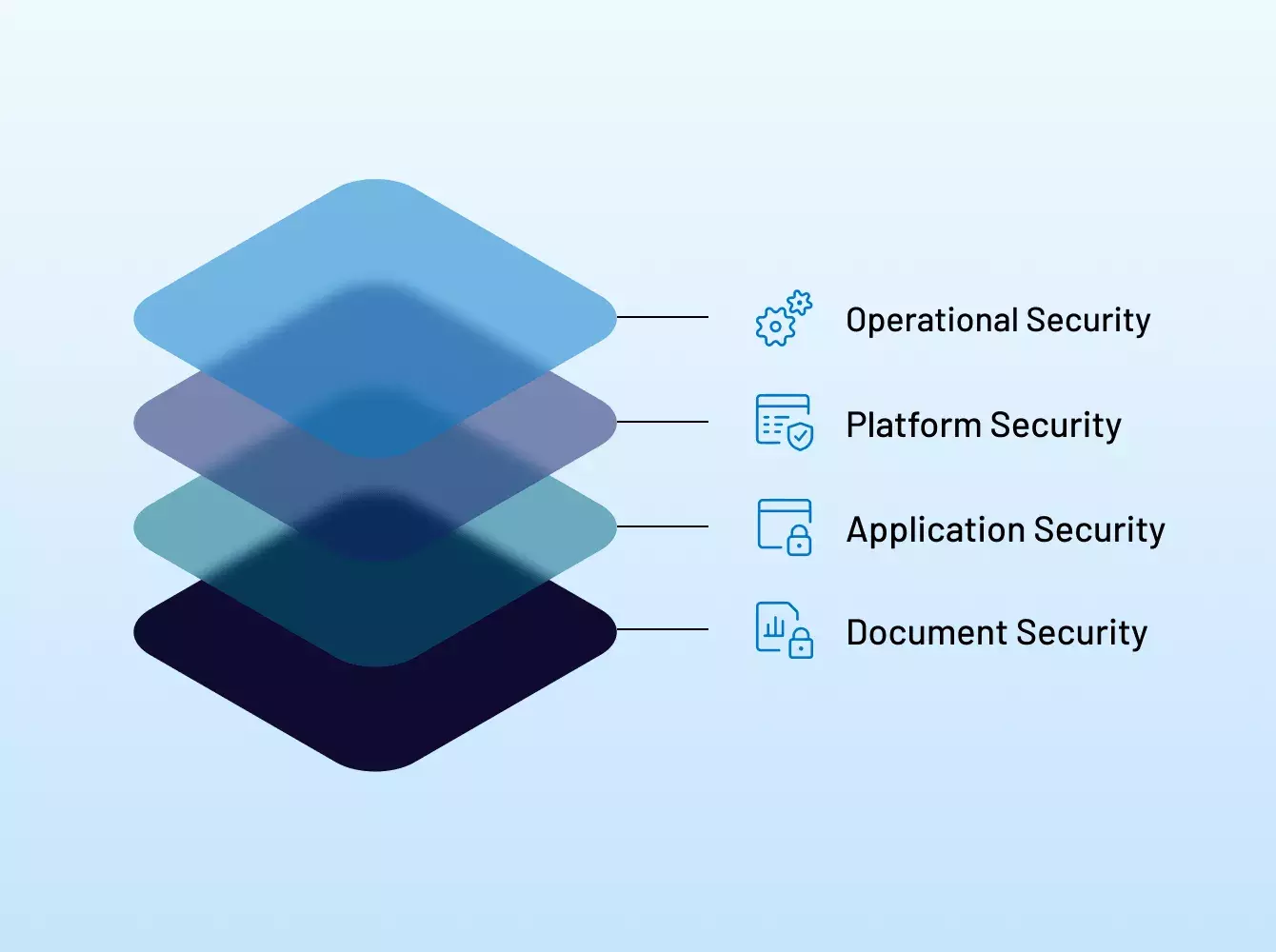
Intralinks es pionera en los virtual data room (VDR) e innova constantemente la manera en que nuestros clientes trabajan con soluciones diseñadas para un fin específico y con una seguridad de nivel bancario para proteger los datos y las reputaciones.
Contamos con el respaldo de SS&C, una empresa de tecnología financiera de primer nivel con ingresos superiores a $6,000 millones.
Mientras nuestros competidores reducen la inversión en R&D y en servicios, nosotros seguimos invirtiendo y hemos destinado más de 200 millones de dólares en cinco años para ofrecer a nuestros clientes una experiencia de primera clase.
¿No son las otras soluciones de uso compartido de archivos igualmente seguras?
No. Mientras que otros proveedores afirman ser seguros, muchos utilizan un lenguaje impreciso y engañoso a propósito para esconder sus verdaderas credenciales de seguridad.
Nuestro enfoque de seguridad integral incluye certificaciones líderes en la industria y las mejores prácticas de cumplimiento que se extienden a todos los aspectos de Intralinks: sus empleados, procesos, políticas e infraestructura de respaldo.
Dé un paso adelante.
- Seguridad líder en la industria
- Alcance y confianza global
- Soluciones versátiles y fáciles de usar
- El mejor soporte en su clase